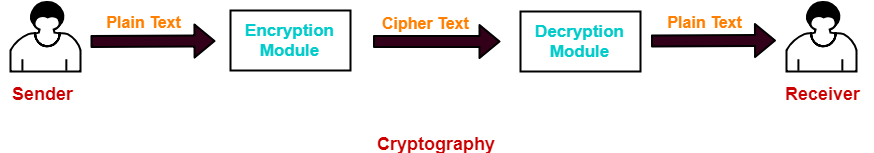
Asymmetric Encryption-
Before you go through this article, make sure that you have gone through the previous article on Asymmetric Key Cryptography.
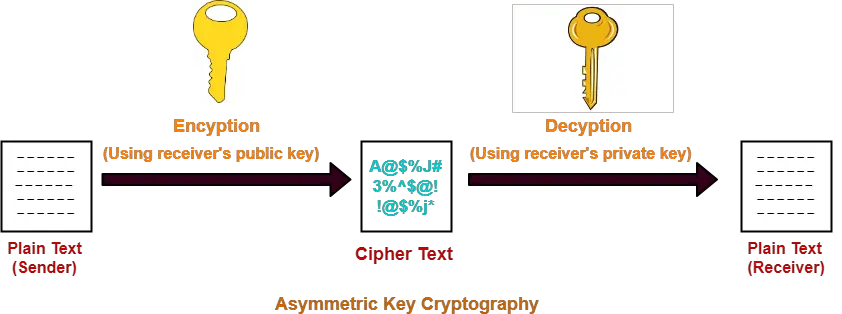
In asymmetric encryption,
- Sender and receiver use different keys to encrypt and decrypt the message.
- The famous asymmetric encryption algorithms are-

In this article, we will discuss about Diffie Hellman Key Exchange Algorithm.
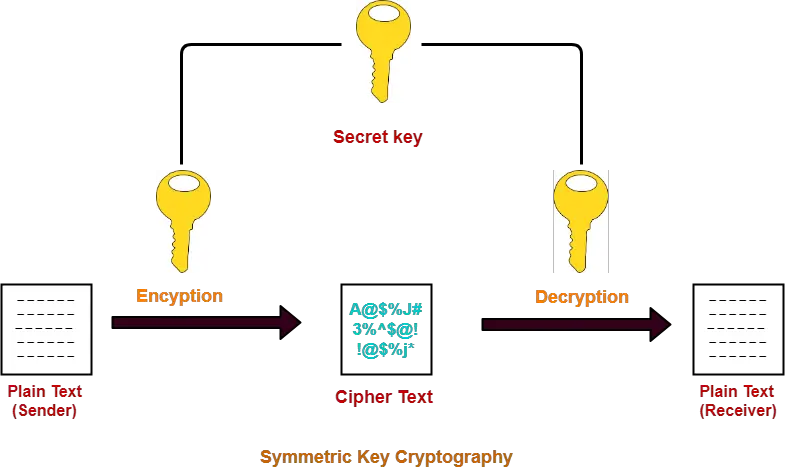
Symmetric Key Cryptography-
In symmetric key cryptography,
- Both sender and receiver use a common secret key to encrypt and decrypt the message.
- The major issue is exchanging the secret key between the sender and the receiver.
- Attackers might intrude and know the secret key while exchanging it.
Read More- Symmetric Key Cryptography
Diffie Hellman Key Exchange-
As the name suggests,
- This algorithm is used to exchange the secret key between the sender and the receiver.
- This algorithm facilitates the exchange of secret key without actually transmitting it.
Diffie Hellman Key Exchange Algorithm-
Let-
- Private key of the sender = Xs
- Public key of the sender = Ys
- Private key of the receiver = Xr
- Public key of the receiver = Yr
Using Diffie Hellman Algorithm, the key is exchanged in the following steps-
Step-01:
- One of the parties choose two numbers ‘a’ and ‘n’ and exchange with the other party.
- ‘a’ is the primitive root of prime number ‘n’.
- After this exchange, both the parties know the value of ‘a’ and ‘n’.
Step-02:
- Both the parties already know their own private key.
- Both the parties calculate the value of their public key and exchange with each other.
| Sender calculate its public key as-
Ys = aXs mod n Receiver calculate its public key as- Yr = aXr mod n |
Step-03:
- Both the parties receive public key of each other.
- Now, both the parties calculate the value of secret key.
| Sender calculates secret key as-
Secret key = (Yr)Xs mod n Receiver calculates secret key as- Secret key = (Ys)Xr mod n |
Finally, both the parties obtain the same value of secret key.
PRACTICE PROBLEMS BASED ON DIFFIE HELLMAN KEY EXCHANGE-
Problem-01:
Suppose that two parties A and B wish to set up a common secret key (D-H key) between themselves using the Diffie Hellman key exchange technique. They agree on 7 as the modulus and 3 as the primitive root. Party A chooses 2 and party B chooses 5 as their respective secrets. Their D-H key is-
- 3
- 4
- 5
- 6
Solution-
Given-
- n = 7
- a = 3
- Private key of A = 2
- Private key of B = 5
Step-01:
Both the parties calculate the value of their public key and exchange with each other.
Public key of A
= 3private key of A mod 7
= 32 mod 7
= 2
Public key of B
= 3private key of B mod 7
= 35 mod 7
= 5
Step-02:
Both the parties calculate the value of secret key at their respective side.
Secret key obtained by A
= 5private key of A mod 7
= 52 mod 7
= 4
Secret key obtained by B
= 2private key of B mod 7
= 25 mod 7
= 4
Finally, both the parties obtain the same value of secret key.
The value of common secret key = 4.
Thus, Option (B) is correct.
Problem-02:
In a Diffie-Hellman Key Exchange, Alice and Bob have chosen prime value q = 17 and primitive root = 5. If Alice’s secret key is 4 and Bob’s secret key is 6, what is the secret key they exchanged?
- 16
- 17
- 18
- 19
Solution-
Given-
- n = 17
- a = 5
- Private key of Alice = 4
- Private key of Bob = 6
Step-01:
Both Alice and Bob calculate the value of their public key and exchange with each other.
Public key of Alice
= 5private key of Alice mod 17
= 54 mod 17
= 13
Public key of Bob
= 5private key of Bob mod 17
= 56 mod 17
= 2
Step-02:
Both the parties calculate the value of secret key at their respective side.
Secret key obtained by Alice
= 2private key of Alice mod 7
= 24 mod 17
= 16
Secret key obtained by Bob
= 13private key of Bob mod 7
= 136 mod 17
= 16
Finally, both the parties obtain the same value of secret key.
The value of common secret key = 16.
Thus, Option (A) is correct.
To gain better understanding about Diffie Hellman Key Exchange Algorithm,
Next Article- Digital Signatures
Get more notes and other study material of Computer Networks.
Watch video lectures by visiting our YouTube channel LearnVidFun.