Access Control in Networking-
Before you go through this article, make sure that you have gone through the previous article on Access Control.
We have discussed-
- Access Control is a mechanism that controls the access of stations to the transmission link.
- Broadcast links require the access control mechanism.
- There are various access control methods-
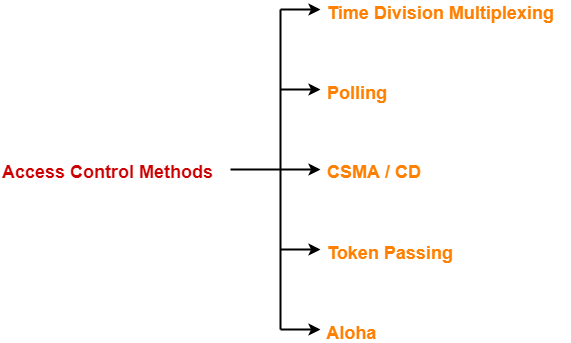
In this article, we will discuss about polling.
Polling-
In this access control method,
- A polling is conducted in which all the stations willing to send data participates.
- The polling algorithm chooses one of the stations to send the data.
- The chosen station sends the data to the destination.
- After the chosen station has sent the data, the cycle repeats.
Example-
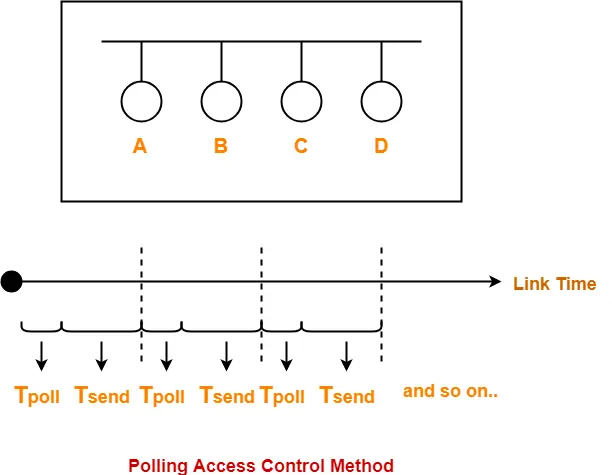
Here-
- Tpoll = Time taken for polling
- Tsend = Time taken for sending the data = Transmission delay + Propagation delay = Tt + Tp
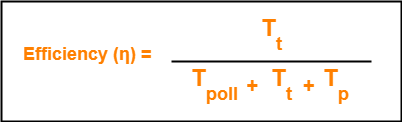
Efficiency-
| Efficiency (η) = Useful Time / Total Time |
- Useful time = Transmission delay of data packet = Tt
- Useless time = Time wasted during polling + Propagation delay of data packet = Tpoll + Tp
Thus,
Advantages-
- Unlike in Time Division Multiplexing, no slot is ever wasted.
- It leads to maximum efficiency and bandwidth utilization.
Disadvantages-
- Time is wasted during polling.
- Link sharing is not fair since each station has the equal probability of winning in each round.
- Few stations might starve for sending the data.
Important Formulas-
- Efficiency (η) = Tt / (Tpoll + Tt + Tp)
- Effective Bandwidth / Bandwidth Utilization / Throughput = Efficiency(η) x Bandwidth
- Maximum Available Effective Bandwidth = Total number of stations x Bandwidth requirement of 1 station
To gain better understanding about Polling Access Control Method,
Next Article- CSMA / CD | Access Control Method
Get more notes and other study material of Computer Networks.
Watch video lectures by visiting our YouTube channel LearnVidFun.